In our previous blog, we continued our journey towards Zero Trust adoption by developing a strategic approach and engaging the right stakeholders. Today, we’ll take the next steps in our journey by examining the business scenario of rapidly modernizing your security posture.
Instead of concentrating on the technical aspects of implementing a Zero Trust architecture, the focus of this blog is on developing a strategy and setting priorities, as well as measuring and reporting progress.
What is Security Posture?
Your security posture refers to your organization’s overall cybersecurity defense capabilities, along with its preparedness and operational readiness to address ongoing cybersecurity threats. Your security posture should be quantifiable and measurable, akin to any other significant metric related to the operational status or well-being of your organization.
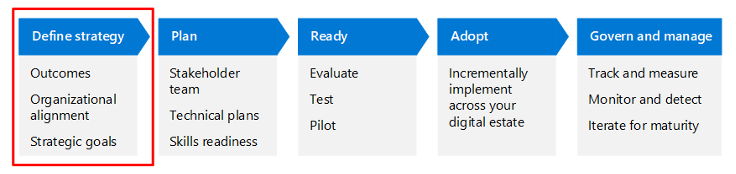
5 Steps to Rapidly Modernizing Your Security Posture
In this blog:
- Defining Your Security Strategy
- Building Your Security Posture Modernization Plan
- Getting Ready to Implement Your Modernization Plan
- Adopting Your Security Posture Modernization Plan
- Governing and Managing Your Security Posture
1. Defining Your Security Strategy
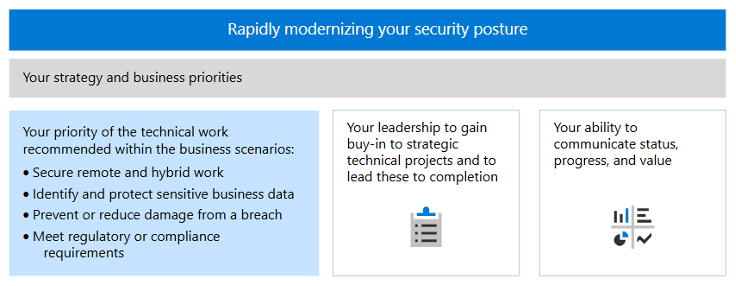
Collaborate within your organization to create a strategy and establish priorities and objectives for your Zero Trust journey, highlighting the significance of organizational alignment and strategic goals.
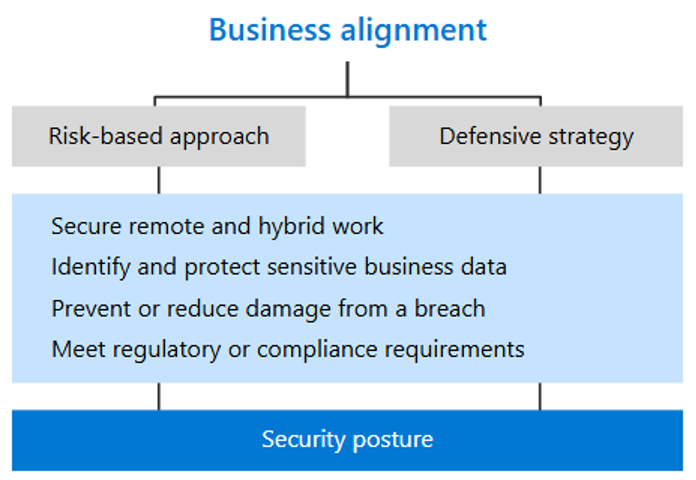
To successfully implement the principles of Zero Trust with your partner teams, it’s essential to achieve business alignment. By agreeing on the risks and gaps in your current security posture, determining the steps needed to mitigate these issues, and establishing a method to track and communicate progress, you can build confidence in your evolving security framework.
Business alignment can be attained through one or both of the following approaches:
- Take a risk-based approach in which you identify the top risks to your organization and the mitigations that are most appropriate.
- Create a defensive strategy, based on understanding where your digital assets are, what they’re composed of, and the relative risk profile based on exfiltration or loss of access to your digital assets.
You can progress through this article using either approach.
Risk-based approach
Some organizations choose to prioritize work and measure progress against risk. Two common tools for identifying risks include tabletop exercises and ISO standards.
Tabletop exercise evaluation: An easy way to get started is to use Six Tabletop Exercises to Help Prepare Your Cybersecurity Team, provided by the Center for Internet Security (CIS).
These tabletop exercises are designed to help organizations walk through different risk scenarios with the goal of evaluating the organization’s state of preparation. They’re each designed to be completed together with your team of stakeholders “in as little as 15 minutes.”
Using ISO standards resources and tools
Many organizations use International Organization for Standardization (ISO) standards resources and tools to gauge an organization’s risk. These provide a structured and comprehensive way for you to review and gauge the risks and mitigations that apply to your organization.
Defensive strategy
When implementing a defensive strategy, it’s essential to assess your entire digital landscape. This involves identifying where your digital assets are located, understanding their composition, and evaluating the risks associated with their potential exfiltration or loss of access.
Next, you should prioritize the areas that need attention by estimating the potential damage each type of incident could cause to your business. Consider these common types of incidents as you evaluate the risks.
- Data loss
- Data leakage
- Data breach
- Data access loss
- Compliance loss due to cyber incident
Once you have identified the key areas that need protection, you can systematically implement Zero Trust principles in those areas. This process will also help you build a solid case for the funding and resources necessary to carry out this work
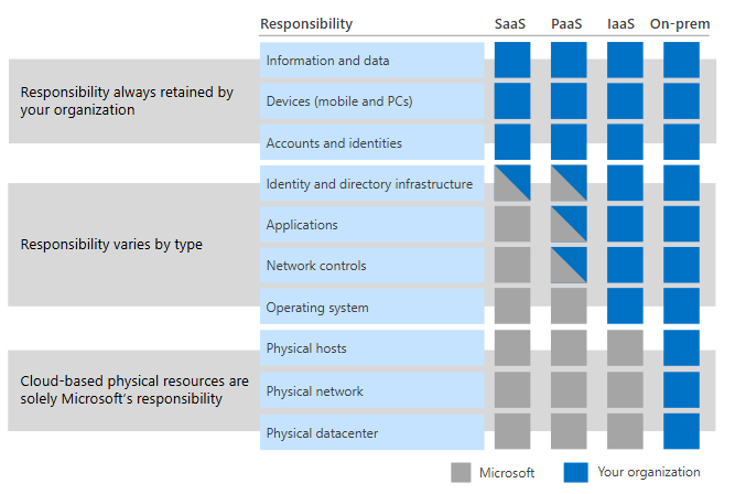
Additionally, the shared responsibility model is a valuable resource for shaping your strategy and priorities. Your security responsibilities will vary depending on the type of cloud service you use. The following diagram illustrates the balance of responsibilities between you and Microsoft.
Tip: Don’t Document and report on your security posture
It’s essential to continuously report on your security posture using various methods, including Microsoft scoring mechanisms and other dashboards. There are numerous tools and approaches available to achieve this. In this scenario, you will identify the reports and tools that are most beneficial for your organization. Additionally, you will develop a documentation method for your security posture that is effective for your specific needs.
2. Building Your Security Posture Modernization Plan
In this phase, you create technical plans and ensure skills readiness. It includes evaluating, testing, and piloting the technical objectives.
This Excel workbook will assign owners and track your progress for these stages, objectives, and tasks. Here’s the worksheet for this business scenario.
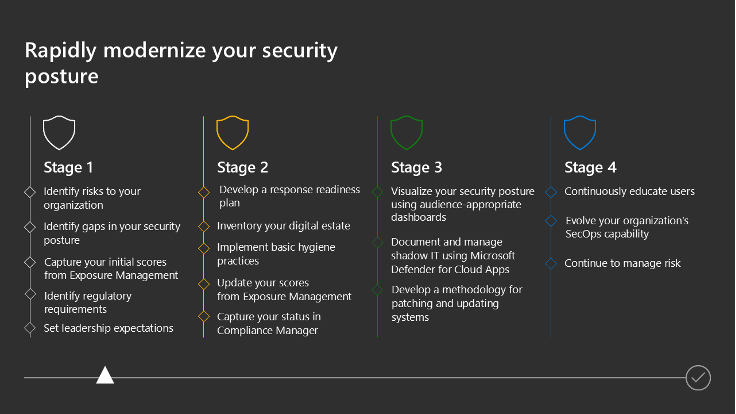
Microsoft provides resources to help you rapidly modernize your security posture. The following sections highlight resources for specific tasks in the four stages defined in the image above.
Stage 1
Here you begin to understand your current security posture. You initiate discussions within your leadership team and organization to learn about Zero Trust and how it aligns with business strategies and objectives.
Stage 2
Here continue to detail your current security posture, including:
- Developing a response readiness plan
- Starting an inventory of your digital estate
- Implementing basic hygiene
- Inventory your digital estate
When preparing for breach readiness, it is essential to understand the state of both your physical and digital assets. The first objective in this process is to take an inventory. It is important to note that other business scenarios may require you to inventory the assets affected by the specific situation. These inventories and the status of the items contribute significantly to your overall security posture.
For this particular business scenario, it is recommended that you compile a comprehensive list of all physical and digital assets, services, and line-of-business (LOB) applications.
Physical assets include endpoints such as mobile phones, PCs, laptops, and servers (whether physical or virtual). Digital assets can encompass services like email and retention data in Exchange Online, files and records stored in SharePoint Online, SQL Platform as a Service (PaaS) offerings, data lakes, and files located on on-premises file servers or Azure File Shares.
To enhance visibility into the services being utilized by users, including shadow IT data locations, consider utilizing a Cloud Access Security Broker (CASB) service, such as Microsoft Defender for Cloud.
The following are digital assets to include in your inventory:
- Identities
- Devices
- Data
- Apps
- Infrastructure
- Network
Stage 3
A robust security posture requires effective instrumentation to enhance visibility. It’s important to consolidate your tools and methods into as few views or dashboards as possible to simplify the process. The primary goal at this stage is to visualize your security posture through dashboards that are tailored to your audience.
Adopting an “assume breach” mentality necessitates an examination of breach preparedness by implementing continuous monitoring. In this phase, it’s essential to document and evaluate the number of portals or views that fulfill this function. This internal documentation can take the form of reports that you compile manually or reports generated from your security tools, such as Exposure Management, Compliance Manager, Microsoft Defender XDR, Microsoft Defender for Cloud, Microsoft Sentinel, and other relevant tools.
For example:
- An executive summary view of risk, breach preparation, and current incidents.
- A CISO summary view for IT and OT security assets.
- Security Analyst views to respond to incidents.
- A historical view on security information and event management (SIEM) and security orchestration, automation, and response (SOAR) to comply with regulatory demands and long-running threat hunting.
- Creating and maintaining role-specific views create transparency with the status of the security posture with your stakeholders who are sharing the burden of security management, from executive leaders through to incident responders.
Stage 4
The objectives of Stage 4 are about maturing your organization’s ability to prevent and respond to attacks.
If you need help building your plan, I encourage you to explore Quisitive’s Cloud Security Assessments, where we evaluate your environments and provide actionable next steps for improving your security posture.
3. Getting Ready to Implement Your Modernization Plan
This phase focuses on gradually implementing the technical objectives across your digital landscape. It entails tracking and measuring progress, monitoring and identifying threats, and iterating for greater maturity.
The Ready phase for this business scenario differs from other business scenarios. Instead of focusing on evaluating, testing, and piloting specific security capabilities or configurations, this phase emphasizes assembling your stakeholder team and collaboratively addressing each stage and objective using an agile approach.
For example, when tackling each objective:
- Assess what is needed to achieve the objective, including identifying the necessary team members.
- Start with a reasonable strategy and test it out.
- Refine the approach based on the feedback and insights gained during testing.
- Pilot the revised approach and make further adjustments based on what you’ve learned.
The following table illustrates how this process can be applied to the objective of identifying risks to your organization in Stage 1 of the Plan phase.
| Ready task | Action |
| Evaluate | Decide what resources you’ll use to evaluate risks and who should be included in the activities. This evaluation can include using the tabletop exercises or the ISO standards. Determine who in your organization should participate. |
| Test | Using the resources you’re targeting, review the recommended exercises with a small set of your stakeholders to gauge your readiness to engage your fuller team of stakeholders. |
| Pilot | If you’re using the tabletop exercises, try out one of the scenarios with the chosen participants. Review the results and determine if you’re ready to proceed to the other exercises. If you’re using the ISO standards, target a portion of the standard to pilot the evaluation. |
By taking an agile approach like this, you allow opportunities to adjust and optimize your methodology and process. You also build confidence as you go.
4. Adopting Your Security Posture Modernization Plan
This phase focuses on systematically guiding each component of your Zero Trust architecture through the adoption lifecycle while governing and managing the implementation process.
During the Adopt phase, you will incrementally implement your strategy and deployment plans across various functional areas. In this scenario, this involves achieving the objectives outlined in the four stages or any customized objectives and stages that apply to your organization. Modernizing your security posture also entails meeting the technical objectives recommended in other business scenarios or those prioritized by your organization, all contributing to your overall security posture.
As you transition to the Adopt phase for this scenario and others, it is essential to communicate the status, progress, and value of your efforts.
5. Governing and Managing Your Security Posture
This section highlights the importance of communicating status, progress, and value to business leaders. It emphasizes the need for a standardized security posture that caters to IT and Operational Technology (OT) security requirements.
Security governance is an ongoing process. As you move into this phase, focus on tracking and measuring the results of each component of the Zero Trust architecture that you have implemented. By combining this with continuous monitoring and detection, you will be able to identify opportunities for improvement and maturity.
Track and Measure
This article provides various reports and dashboards that you can utilize to evaluate your current status and measure progress. Ultimately, the goal is to establish a set of metrics that demonstrate your advancements and help identify potential emerging vulnerabilities. Use these different reports and dashboards to gather the metrics that are most relevant to your organization.
Team and Organization Metrics
The following table lists some example metrics that you can use to monitor your team’s and organization’s security posture.
| Business Enablement | Security Posture | Security Response | Security Improvement |
| Mean time for security review | # of new apps reviewed | Mean time to recover (MTTR) | # of modernization projects open |
| Average boot and sign-in time for managed devices | % of compliant apps | Time to restore critical systems | Number of repetitive manual steps removed from workflows |
| Number of security interruptions in user workflow | # of privileged accounts meeting 100% of requirements | # of high-severity incidents | # of lessons learned from internal and external incidents |
| % of IT helpdesk time spent on low-value security activities | # of accounts meeting 100% of requirements | Incident growth rate (overall) |
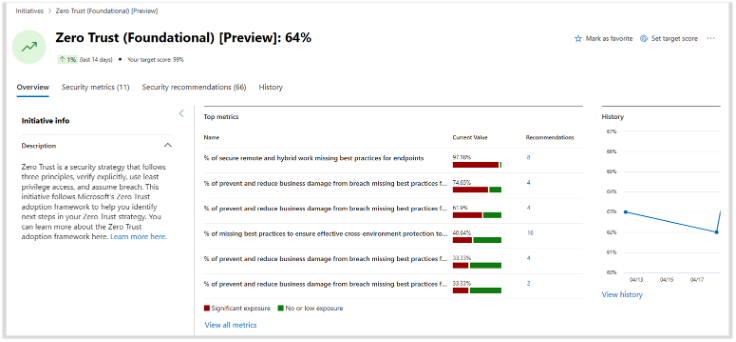
Microsoft Security Exposure Management is a security solution that provides a unified view of security posture across company assets and workloads. Within this tool, Security Initiatives help you assess readiness and maturity in specific areas of security risk. Security Initiatives take a proactive approach to managing security programs towards specific risk or domain-related objectives.
This Zero Trust adoption framework encourages a risk-based approach or a defensive strategy. With either approach, you can focus on other security initiatives within the exposure management tool, such as Ransomware Protection or specific threat initiatives, allowing your efforts to contribute to the overall maturity of the Zero Trust initiative.
You can utilize the Zero Trust initiative alongside this adoption framework. The metrics and tasks associated with the initiative are organized by specific Zero Trust business scenarios.
Monitor and detect
As you navigate each business scenario, determine how you will monitor and detect changes in the environment and potential breaches. Many of the monitoring and detection capabilities are offered through Extended Detection and Response (XDR) tools, including Quisitive’s Managed Detection and Response.
Iterate for maturity
Implementing Zero Trust is a journey that can take years, especially in large organizations. During this time, attackers will continue to evolve their techniques. Therefore, it’s crucial to utilize your metrics alongside your monitoring and detection capabilities to identify areas where you need to improve and advance your Zero Trust environment. Additionally, make sure to continuously evaluate and adapt how you measure success, as well as how you communicate progress, status, and value.
Conclusion
Embracing a Zero Trust strategy is crucial for small and medium-sized businesses (SMBs) to strengthen their security on Azure. By establishing a clear strategy, aligning it with business objectives, and systematically implementing security measures, organizations can effectively reduce risks and safeguard their digital assets. It is also important to continuously monitor, assess, and adapt your security practices to keep up with evolving threats.
Thank you for reading! If you find this blog helpful, be sure to stay tuned for future installments where we dive deeper into enhancing your security posture.

;)