With the advancements of automation in scanning and code development, cyber threat actors are broadening their scope and potentially having a significantly smaller entry cost. Small to medium-sized businesses (SMBs) face increasing cyber threats, making robust security measures more critical than ever, as they often become the defenders of not only their information but that of their clients as well.
Azure provides a scalable and secure platform for SMBs to protect their data and operations. However, there is a shared responsibility in implementing and managing these environments.
This blog will explore Azure security best practices, emphasizing their business value and providing practical insights for implementation. Azure security is essential for SMBs due to the rising number of cyber threats targeting these businesses.
In this blog:
- Zero Trust Guidance
- Defender for Cloud
- Enabling MFA
- Infrastructure-as-Code
- Defining the Business Value of Azure Security
- Additional Tools for Enhanced Azure Security
- Quisitive Spyglass: Managed Azure Security Services
Azure Security Best Practice #1: Zero Trust Guidance
One of the foundational principles of Azure security is implementing a Zero Trust Architecture. Zero Trust operates on the principle of “never trust, always verify,” meaning that every access request is thoroughly vetted regardless of origin. SMBs can apply these principles using Azure tools such as Azure Entra ID (previously known as “Azure Active Directory”) and Conditional Access policies. These tools help enforce strict access controls, ensuring only authorized users can access sensitive data and resources. For more detailed guidance on Zero Trust, visit Microsoft’s Zero Trust guidance for SMBs.
The three main principles of a Zero Trust (ZT) methodology as described below, is just the first layer of your ZT strategy.
| Principle | Description |
| Verify explicitly | Always authenticate and authorize based on all available data points. |
| Use least privilege access | Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection. |
| Assume breach | Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses. |
Each of these principles are then applied to the architecture of your technology stack and divided into 7 different technology pillars: Identify, endpoints, data, apps, infrastructure and network.
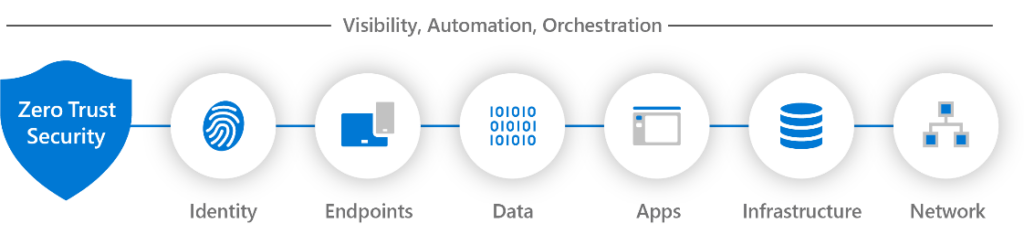
The approach is applied in such a manner that you provide the least privilege of access to the technology pillar for the components that need to communicate. As they communicate, they need to be authenticated and ensure that they are authorized to access the required components. The final element of this strategy functions on the concept that you assume breach, even of your internal environment. Therefore, you would want to minimize the blast radius if a component is compromised, segment access, and protect communications between components, any analytics, and monitors, and actively hunt in your environment for potential anomalies, indicators of compromise, and indicators of exfiltration.
A great resource to learn about the Zero Trust approach in an agile environment is “The Unicorn Project: A Novel about Developers, Digital Disruption, and Thriving in the Age of Data” by Gene Kim. This is a compelling novel that follows the journey of Maxine, a talented lead developer and architect, who is blamed for a major outage and subsequently exiled to work on the troubled Phoenix Project. Set in the same universe as “The Phoenix Project,” this story delves into the challenges of a DevOps transformation within a large corporation. Through Maxine’s experiences and her collaboration with a team of corporate rebels, the novel introduces the Five Ideals: Locality and Simplicity; Focus, Flow, and Joy; Improvement of Daily Work; Psychological Safety; and Customer Focus. These ideals serve as a blueprint for achieving a positive and lasting business, technology, and cultural transformation, highlighting the importance of developer productivity, organizational agility, and customer-centricity in the age of digital disruption.
Azure Security Best Practice #2: Defender For Cloud
Defender for Cloud, previously branded as “Azure Security Center” is another critical component for SMBs. It provides unified security management and advanced threat protection across hybrid cloud workloads. It helps monitor and manage security across Azure services, offering recommendations and insights to improve security posture. By leveraging Defender for Cloud, SMBs can gain visibility into their security status and take proactive measures to address vulnerabilities.
It provides a comprehensive security management system with unified security monitoring and advanced threat protection across hybrid cloud workloads. It helps small to medium-sized businesses (SMBs) enhance their security posture by offering continuous assessment of security configurations, providing actionable recommendations, and enabling automated responses to threats. SMB leaders can leverage Defender for Cloud to gain visibility into their security status, identify and mitigate vulnerabilities, and ensure compliance with industry standards. By using its built-in tools and integrations, such as Azure Defender for Cloud and Azure Policy, SMBs can proactively manage their security, reduce risks, and protect their critical assets from cyber threats. Learn more about setting up and using Defender for Cloud here.
Azure Security Best Practice #3: Enabling MFA
Enabling Multi-Factor Authentication (MFA) is crucial for protecting against unauthorized access. MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access, significantly reducing the risk of compromised credentials. Azure offers various MFA methods, including the Microsoft Authenticator app, which can be easily enabled for all users. Detailed steps for enabling MFA in Azure can be found here.

Integrating outside Cloud Service Provider (CSP) identities with Azure Entra ID can significantly enhance your organization’s security and collaboration capabilities. Azure Entra External ID allows you to securely work with people outside your organization, whether they are external partners, consumers, or business customers. This integration supports a variety of identity providers, including corporate or government-issued accounts and social identity providers like Google or Facebook.
You can use Microsoft Entra External ID for B2B collaboration to get started. This allows you to invite external users to access your enterprise apps through invitation or self-service sign-up. You can manage the level of access these guests have to your resources, ensuring secure collaboration. Detailed information on Microsoft Entra External ID can be found here.
For managing cross-tenant access, Microsoft Entra External ID provides settings to control inbound and outbound access. These settings allow you to trust multifactor authentication (MFA) and device claims from other organizations, facilitating secure collaboration across different Microsoft Entra organizations and Azure clouds. More details on cross-tenant access settings are available here.
By leveraging these capabilities, you can ensure that external identities are securely integrated into your Azure environment, enhancing security and collaboration.
Azure Security Best Practice #4: Infrastructure-as-Code
This might be a little more advanced of a topic. This section is for those who might be going down the everything-as-code or infrastructure-as-code (IaC) route. This is using a top-down approach of setting guidelines from the subscription level down.
1. Regular Security Assessments
Regular security assessments and compliance checks are vital for maintaining a strong security posture. Ongoing assessments help identify vulnerabilities and ensure compliance with industry standards. Azure Policy and Azure Blueprints can automate compliance checks and enforce security policies, making it easier for SMBs to stay compliant.
For more information on conducting security assessments and compliance checks, visit Azure’s operational security best practices. Azure Policies and Blueprints are potent tools that can significantly benefit small—and medium-sized businesses (SMBs) by enhancing their security, compliance, and operational efficiency.
2. Azure Policies
Azure Policies help SMBs enforce organizational standards and assess compliance at scale. By defining policies, you can ensure that your resources comply with corporate standards and service level agreements.
For example, you can create policies to enforce the use of specific virtual machine sizes, ensure that storage accounts are encrypted, or restrict the deployment of resources to particular regions. This helps maintain consistency across your environment and reduces the risk of misconfigurations that could lead to security vulnerabilities.
Azure Policies also provide real-time compliance assessments, allowing you to identify and remediate non-compliant resources quickly. More information on Azure Policies can be found here.
3. Azure Blueprint
Azure Blueprints enable SMBs to define a repeatable set of Azure resources that implement and adhere to an organization’s standards, patterns, and requirements. Blueprints allow you to orchestrate the deployment of various resource templates and other artifacts, such as role assignments, policy assignments, and Azure Resource Manager (ARM) templates. This ensures that new environments are set up consistently and comply with organizational policies.
For instance, you can create a blueprint that includes a virtual network, a set of policies for security and compliance, and role assignments for access control. This blueprint can then be applied to multiple subscriptions, ensuring that all environments are configured consistently.
Azure Blueprints also support versioning, making updating and managing changes across your environments easy. Detailed information on Azure Blueprints is available here.
Note: Azure Blueprint is scheduled to be depreciated in July 2026 and integrated into Azure Resource Manager as TemplateSpecs and DeploymentStacks.
4. Desired State Configuration (DSC)
Desired State Configuration (DSC) is a management platform in PowerShell that enables the deployment and management of configuration data for software services and environments. It uses a declarative model to define a system’s desired state, ensuring that configurations are consistent and repeatable. DSC helps automate the maintenance of servers’ correct configuration, reducing scripting complexity and minimizing errors. By separating the configuration intent from the execution logic, DSC allows for more efficient and reliable IT infrastructure management.
Another tool to note is the Microsoft Cloud Security Baselines, which provide standardized security guidelines for Azure services that align with industry standards like NIST and CIS. These baselines offer detailed recommendations on security configurations, feature availability, and optimal practices to enhance cloud security. Each baseline includes control areas such as network security, identity management, and privileged access, ensuring comprehensive coverage of security aspects. Organizations can strengthen their cloud security posture by following these baselines and leveraging tools like Microsoft Defender for Cloud to monitor compliance and implement necessary configurations.
By leveraging these tools in Azure, SMBs can streamline operations, ensure compliance with industry standards, and enhance their security posture. These tools provide a robust framework for managing and governing Azure resources, helping SMBs achieve operational excellence and reduce the risk of security incidents.
Defining the Business Value of Azure Security
The business value of Azure security extends beyond technical benefits. Robust security measures can lead to significant cost savings by preventing breaches, which can be financially devastating for SMBs. Additionally, strong security practices enhance customer trust and business reputation, providing a competitive advantage. Case studies of SMBs successfully implementing Azure security solutions demonstrate real-world benefits and outcomes. Explore these case studies and their impact here.
Technical implementation strategies are essential for effectively utilizing Azure security features. A step-by-step guide to setting up Azure Security Center includes configuring security policies, monitoring alerts, and integrating with other Azure services. Best practices for configuring MFA involve enabling it for all users and using Conditional Access policies to enforce MFA requirements. Azure Sentinel can automate threat detection and response, reducing the burden on IT teams and improving overall security. Detailed implementation strategies can be found here.
Staying updated with security trends is crucial for SMBs. The cybersecurity landscape is constantly evolving, and new threats emerge regularly. Azure’s security features are designed to address these threats, but continuous learning and training in cybersecurity are essential. Resources such as Microsoft Learn offer valuable information and training materials on Azure security, helping SMBs stay informed about the latest security trends. Access these resources here.
Conclusion
In summary, SMBs can immediately take several actionable steps to improve their security posture. These include enabling MFA, conducting regular security assessments, and using Azure Security Center to monitor and manage security. Long-term strategies for maintaining robust security involve adopting a zero-trust approach and investing in ongoing training and education. For further reading and resources on Azure security, visit Microsoft Learn.
Following these Azure Security best practices, SMBs can ensure their Azure environment is secure, protecting their data and operations from cyber threats. Implementing these strategies will enhance security and provide significant business value, helping SMBs thrive in a digital world.
Additional Tools for Enhanced Azure Security
Azure offers a variety of tools designed to enhance security and protect your business from cyber threats:
- Azure Key Vault is a cloud service that safeguards encryption keys and secrets like certificates, connection strings, and passwords. By centralizing the storage of application secrets, Azure Key Vault helps control their distribution and reduces the risk of accidental exposure.
- Azure DDoS Protection protects against Distributed Denial of Service (DDoS) attacks. It automatically detects and mitigates DDoS attacks in real-time, ensuring your applications remain available and performant. This service is integrated with Azure’s global network, providing comprehensive protection for your resources.
- Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It provides a centralized way to enforce network security policies across multiple subscriptions and virtual networks. Azure Firewall uses a static public IP address for your virtual network resources, allowing outside firewalls to identify traffic from your virtual network.
- Purview Information Protection (previously known as “Azure or Microsoft Information Protection) helps organizations classify, label, and protect data based on its sensitivity. This tool integrates with Microsoft 365 and other Azure services for comprehensive data protection. It allows you to apply labels to documents and emails, ensuring that sensitive information is handled appropriately.
- Azure Bastion provides secure and seamless RDP and SSH connectivity to your virtual machines through the Azure portal. This eliminates the need for a public IP address on your virtual machines, reducing exposure to the internet and enhancing security.
By leveraging these additional Azure tools, SMBs can further enhance their security posture, ensuring comprehensive protection against a wide range of cyber threats. Combined with the best practices outlined earlier, these additional tools can help to provide a robust framework for securing your Azure environment and safeguarding your business.
Improve Your Azure Security Posture with Quisitive Spyglass
Should you need assistance implementing these security processes and tooling, the Quisitive Spyglass Security program can help you mature your security posture with ongoing security coaching and technical implementation resources using our Flex-hours approach.

;)



