Happy October and Happy Halloween! Since October is Cybersecurity Awareness Month, I made a personal commitment at the beginning of the month to post at least one tweet per day on the topic of security tips, awareness, and/or guidance. I had some fun with this, waking up every morning and thinking, “What helpful thing could I offer today?”
I hope that these little bits of security awareness tips and guidance can help colleagues, friends, customers, and casual passers-by. As you’ll soon see these tips span across the main tenets of information security including Identity, Data, Device, Application, and Access.
Let’s jump into our cybersecurity awareness tips!
#1: Use Passphrases instead of passwords
A passphrase is the same as a password, but harder to crack, while easy to remember!
“Apitsaap,bhtc,wetr”! <— Here’s one made from the sentence above!
#2: Multi-Factor Authentication
Does your company use multi-factor authentication (MFA) to protect user accounts? You should!
Microsoft says 99.9% of account-compromise incidents they have dealt with could have been blocked by using an MFA. It works!
#3: Don’t reuse passwords
Do you reuse the same password for all of your accounts? Don’t do that!
Create unique, complex passwords for each of your accounts, use a good password management tool (e.g., 1Password, LastPass, or other) to manage them.
#4: Consider password-less authentication
Did you know that “password-less authentication” greatly improves user-experience, security, and eliminates password threats. Password theft isn’t possible with password-less authentication because they would no longer be part of the equation.
#5: Don’t forget to look at where your email is coming from.
When reading/responding to email, slow down! Check sender’s email address, any links in the body, (hover over them to see reality) before opening any attachments. Even then, if an email looks strange (especially from a coworker or boss) then call them!
#6: Use PIM and MFA to protect privileged user accounts
Protect privileged user accounts by implementing PIM (privileged identity management) & MFA (multi-factor authentication) for all admin accounts. It takes the rug out from under lateral movement attacks & it’s good practice. Ask us how!
#7: Avoid public USB charging stations
Be careful when charging your phone and devices on public USB charging stations because your data can easily be exploited. It’s called juice jacking. Get a USB data blocker to isolate your data from the charging station.
#8: Use RFID Blocking Sleeves on your cards
Always keep your credit cards stored in RFID Blocking Sleeves or a wallet with protection built in. Bad guys can steal your identity and money just by walking beside you. It’s called RFID skimming. Sleeves and RFID wallets prevent this.
#9: Keep your devices up to date
Keep your devices updated to the latest patch levels. You can set auto updates for your personal devices. Your work may have a different process. The more vulnerabilities you have, the bigger the target you become.
#11: Zero Trust
Did you know that password-less authentication, device management, removal of legacy protocols, and risk-based conditional access rules all interact seamlessly to improve user experience, strengthen security posture, and apply Zero Trust principals?
#12: Be weary of unprompted calls from the bank
Picture this: The bank calls and asks you to confirm the 6-digit code in the text message your phone just received. But you didn’t do anything that would have triggered the bank to send the code.
When you receive a call like this, hang up and reset your password immediately. That caller? A bad actor, NOT the bank. Your account was compromised, and the bank’s MFA saved you! #Security
#13: The cloud is more secure than a traditional data center
Your users, data, apps, and IT infra are more secure in a properly configured cloud, like Microsoft 365, Azure, or Dynamics 365, rather than your data center. We can help you envision it, see it, biz-justify it, and execute!
#14: Read closely and stay alert!
Sometimes, lessons are learned from our failures. I clicked! I was caught by a simulated phishing test my company ran. Even us pros fail! The message: link to an internal SharePoint site – something I see routinely. Be sure to read messages and sender addresses closely for signs of malintent.
Learn to spot phishing emails: Subtle things like a misspelled domain in the sender’s address or link, poor grammar in the body, and aggressive wording to get you to click. The better you spot phishing, the less you’ll fall for it.
#15: You don’t have to answer to anyone you don’t know
Be aware both in and out of work regarding conversations by email, phone, or in-person where you’re asked for detail outside of your area of responsibility. Remember, you DON’T HAVE to answer to anyone you don’t know.
#16: Make sure you’re properly managing your client’s sensitive data
Did you know an email or file with credit card details, spreadsheets with clients’ credit cards, or equivalent information sitting unprotected on your systems violates PCI-DSS? You can be banned from taking credit cards as a form of payment to your business.
#17: Be careful with the information you share online.
If you’re a C-level exec who’s traveling, going on vacation, or attending a special VIP event, try not to tweet about it so much! Bad guys use this intel to conduct fraud, fake wire transfers, and impersonation attacks against your company.
#18: We’re all part of the solution! Learn how you can help protect yourself and your company.
I suggest you view this very insightful short video entitled, “Can you recognize the 7 stages of a cyberattack?”
We are all part of the cybersecurity solution! Watch here: http://ow.ly/pYrq50LbOz1
#19: Do your research when choosing a VPN
Using VPN is good, except when it’s hosted by the bad guys!!! It can reveal everything you’ve got.
Be careful when choosing a personal VPN (free could be costly). Best to use only VPN services offered or approved by your company.
#20: Leave stray USB sticks where you find them!
Find a USB thumb drive on the ground in your workplace parking lot? Don’t plug it into your PC!
Sure, you’re curious to see what’s on it. Exactly what the bad guys want. Plug it in, and presto! The bad guy is in! Like a teleporter for malware.
#21: There are ethical hackers out there that can test your corporate environment
Around 40% of ethical hackers (good guys), says SANS Institute, can break into most environments they test, if not all. Nearly 60% said they need less than 5 hours to break into any corporate environment once they find a weakness.
#22: Know where to find news on data breaches in healthcare
If you’re in healthcare, listen up… Did you know that a breach of unsecured protected health information (PHI) of 500 or more individuals, requires you to report to US HHS and get on the “wall of shame”?
Check it out here: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
Also, with curiosity to see the patterns, I quickly created a PowerBI report to visualize the entire historical record of HHS reported breaches of all types from 2009 through 2022. Yikes!
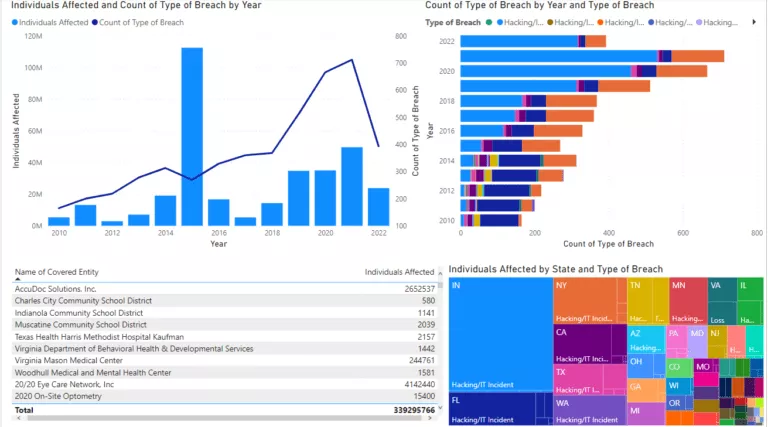
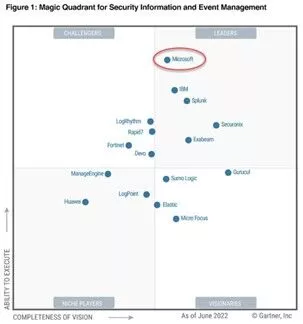
#23: Microsoft Sentinel
Great seeing the results of Microsoft’s dedication, rigor, investment, veracity, and excellence in cybersecurity payoff. Look where Microsoft Sentinel landed on Gartner’s SIEM magic quadrant.
#24: Don’t give out your password or pin – even if it looks like your bank is asking!
Neither your bank nor your IT department should ever ask for your password or PIN. These are “something you know”, meaning only you. Be concerned, and don’t give in, if anyone ever asks for your password or PIN.
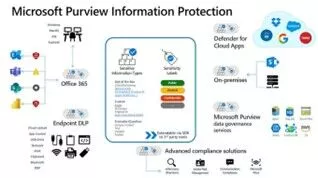
#25: Microsoft Purview Information Protection
Did you know that with Microsoft Purview Information Protection, you can automatically tag (classify) and protect (e.g. restrict exfil, encrypt at rest, restrict display, etc.) any sensitive data in your enterprise?
#26: Be aware of non-technical security
Incident Response is more than just technology solutions. That’s one part.
Other parts include non-technical things: who’s your team, who does PR, when to bring in your legal team, do you practice, etc? Ask us!
#27: Use an Incident Response Framework
Here’s a good overview of the two most common Incident Response frameworks, NIST and SANS Institute. We help clients choose a framework that fits best, then implement, test, and learn. Check it out here: 2021 Incident Response Steps for NIST and SANS Framework | AT&T Cybersecurity (att.com)
#28: Check to see if you’ve been subjected to a data breach
Data breaches happen, sadly, much too often. Ever wonder if your email address (commonly User ID) or phone were among the breached data? Well, check this tool out: HaveIBeenPwned.com
This great website helps us all stay alert!
#29: Encrypt your WiFi
Work at home? You may think encrypting your home Wi-Fi is unnecessary. You’ve got nothing to hide, right? Think again! Your home Wi-Fi can be a “bad-guy pipeline” to your work via your home PC. Encrypt your Wi-Fi with WPA-2.
#30: Cybersecurity awareness training
Does your company do cybersecurity awareness training? Does it periodically phish test to see who reports or who clicks? It should! We do at Quisitive. We learn and develop muscle memory to spot these better and faster. Ask us!
#31: Make sure you trust the apps you’re downloading to your phone
Be leery about installing any apps on your smartphone that come from random websites, email, or Facebook ads. Bad actors often bury data-stealing malware inside benign-looking utility apps. Be careful!
Bonus: Keep personal information safe
If you must store sensitive personal information (PII, PHI, PCI), then properly protect it: classify, encrypt, limit access, and properly dispose of it when it’s no longer needed.
Bonus: Learn to spot phishing attempts
Worth repeating since 90% of all data breaches have a phishing component. Learn to spot phishing: misspelled domain in sender’s address or link, poor grammar, aggressive wording. Get good at it!
Learn more with this article from the IAPP.
Cybersecurity awareness is incredibly important.
If you need assistance with your business’ security strategy, Quisitive can help. Explore our Security and Compliance services.
Until next time,
Ed

;)


