In 2020, COVID dramatically shifted how and where people work. This period of time in our history forced us to think differently. Many businesses survived as a result of outside-the-box thinking and strategies surrounding remote work and adoption of cloud services.
Over the last few years, many businesses have even further accelerated these strategies and some have forged a balance of coming back into the office and remote work. Everyone reading this understands it, as you were affected in one way or another.
Enough of the setup, now to the content…
Bad actors have nearly perfected their attacks on remote workers. With the increase in both number and types of devices that now interact with corporate systems and IT, there’s more opportunity for attacks than ever.
For example, it is relatively commonplace that we use our personal smartphone to interact with work: to check emails, e-sign a document, create documents, communicate with our work-family and our clients, etc.
Over recent years and especially this past calendar year, our Spyglass Security & Compliance team, during the delivery of our Security Assessments, has also witnessed explosive increases in the adoption of remote collaboration applications such as Microsoft Teams, Zoom, Hangouts, and many other apps.
Crucial for this post, is the reference to “many other apps”
How workers access company resources warrants even more focus for businesses than ever, and here’s why: While legitimate application use (e.g., Teams, Zoom, Hangouts, etc.) has accelerated and enabled employees to be productive remotely and remain connected to co-workers regardless of location and time of day, attackers have focused on application-based attacks to gain unauthorized access to your corporate data. This is where the “many other apps” need to be scrutinized carefully, as some could be very malicious.
While most workers deserve kudos for getting better at detecting attacks that target them such as email phishing or credential compromise, there are application-based attacks such as consent phishing that are a significant threat vector to be aware of.
What is a consent phishing attack?
Consent phishing attackers trick users into installing a application of their personal devices. They do this via traditional phishing, ads on social media, via other websites, etc. The application usually has an attractive gimmick: something that the victim might be innocently attracted to. The user downloads and installs the application on their smartphone (or smart device).
The user, in their desire to use the app, authenticates to the workplace via the application. This action grants the app access to sensitive data or other resources.
Instead of stealing the user’s username and password, which was also accomplished in that action, the bad actor is leveraging the attacker-controlled app and the access to exfiltrate valuable data. They will then sell the stolen credentials or use them to carry out another attack (typically impersonation, bot campaign, or other
Discovering consent phishing attacks
Our Spyglass services team works with our clients to help continually improve security posture while enabling more collaboration (securely). Functionally, we provide assistance to identify threats such as consent-phishing among many and implement protections for them, in order to reduce the risks of such attacks.
When we meet many new clients, usually through our award-winning M365 Security Assessment, we consistently identify malicious apps interacting with client’s Office 365 environments due to underutilized security features (or misconfigured tools) especially in the area of Cloud App Security, Device Management, Mobile Device Management, as well as App Sanctioning controls. We have seen many consent phishing attacks successfully carried out on victim users via their personal smart device.
Below is an illustration of one such (and common) consent phishing attack. Notice that an application named: Email from a publisher named: Test, was consented (allowed or authenticated successfully) by a user. They are now is actively interacting via OAuth with Office 365 targeting contacts, data, and other potentially sensitive information using the access levels assigned to the user. Basically this means that the application, while merely an example, is exfiltrating all data from the corporate environment to the bad-actor using the victim’s access level.
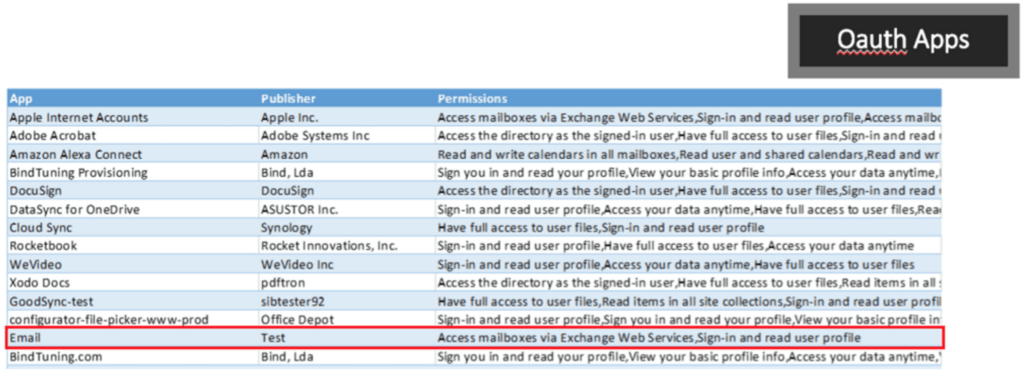
Consent screening from our M365 Security Assessment reveals that a user installed an application on their smartphone (the brand of device or particular app store is irrelevant here). When the user authenticates to their workplace, then the application is granted access equivalent to that of the user’s access. For example, if the victim is a power user or a C-level executive who can access literally any data in the corporate network (not a best practice, by the way), then the application obtains the same level of access: email, SharePoint, OneDrive, file shares, databases, etc.
Consent phishing attacks are common. Unfortunately, we often find successful attacks like that when we perform our M365 Security Assessment for new clients.
As I have said forever, “the findings may be scary, but once we understand them, then we can protect you”.
How to protect your organization from consent phishing attacks
With Microsoft’s integrated security stack, we are able to identify and take measures to remediate malicious apps by disabling them and preventing users from accessing them.
Educate those in your organization on phishing tactics:
- Check for poor spelling and grammar. If an email message or the application’s consent screen has spelling and grammatical errors, or if it demands something urgently, is unexpected, or looks too good to be true, then it’s likely to be suspicious.
- Keep a watchful eye on app names and domain URLs. Attackers like to spoof app names that make it appear to come from legitimate applications or companies but drive you to consent to a malicious app. Make sure you recognize the app name and domain URL before consenting to an application.
- Check out Attack Simulator and Training or ask Quisitive to show you how this can work for you, and/or implement it for you.
Promote and allow access to apps you trust:
- Promote the use of applications that have been publisher-verified. Publisher verification helps admins and end-users understand the authenticity of application developers. Just because it’s from the “app store” doesn’t mean it’s safe.
- Configure application consent policies by allowing users to only consent to specific applications you trust, such as application developed by your organization or from verified publishers.
Educate your organization on how your permissions and consent framework works:
- Understand the data and permissions an application is asking for and understand how permissions and consent works within Office 365.
- Ensure administrators know how to manage and evaluate consent requests.
- Audit apps and consented permissions regularly in your organization to ensure applications being used are accessing only the data they need and adhering to the principles of least privilege.
The increased use of cloud applications has demonstrated the need to improve application security. For additional best practices and safeguards review Microsoft’s Detect and Remediate Illicit Consent Grants in Office 365 and Five steps to securing your identity infrastructure which provide additional good guidance based on best-practices.
Need help identifying potential security gaps in your digital workplace? Explore our Microsoft 365 Security Assessment.
Hope this helps. Stay Safe.
Until next time,
Ed

;)