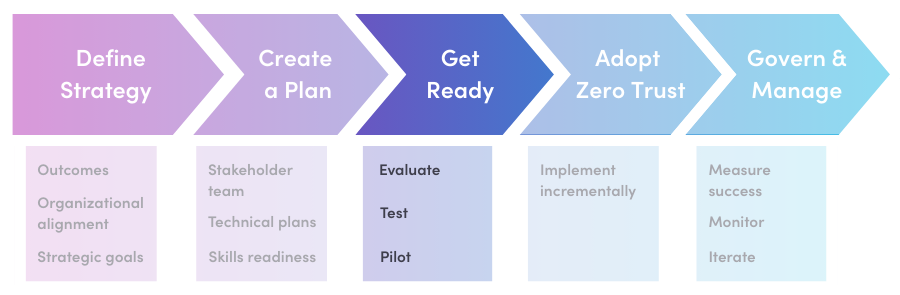
In the last blog in this series, I highlighted the importance of implementing a Zero Trust Security Model in remote and hybrid work environments. I outlined a phased approach for adopting Zero Trust using the Cloud Adoption Framework for Azure:
- Define Strategy: Specify successful outcomes & align the organization
- Create a Plan: Identify stakeholders, create technical plans, and understand required skills
- Get Ready: Evaluate current standing and test your plan
- Adopt Zero Trust: Implement your strategy across your environment and organization.
- Govern and Manage: Monitor your environment and iterate for continuous improvement.
I discussed the first two phases, Define Strategy and Create a Plan, in detail. In this blog, we’ll continue our deep dive and examine the final three phases of the Zero Trust Adoption Framework: Get Ready, Adopt, and Govern & Manage.
Stage 3: Get Ready to Implement Zero Trust for Secure Remote Work
To secure remote and hybrid work, assess and protect identities, devices, and data over the networks in use. Start with small projects that leverage existing licenses and have minimal user impact. Build and test a plan, then roll out new configurations incrementally to improve based on learned lessons. Develop a communication plan to announce changes during deployment.
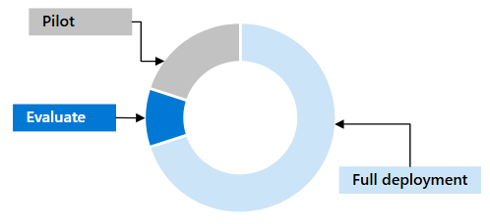
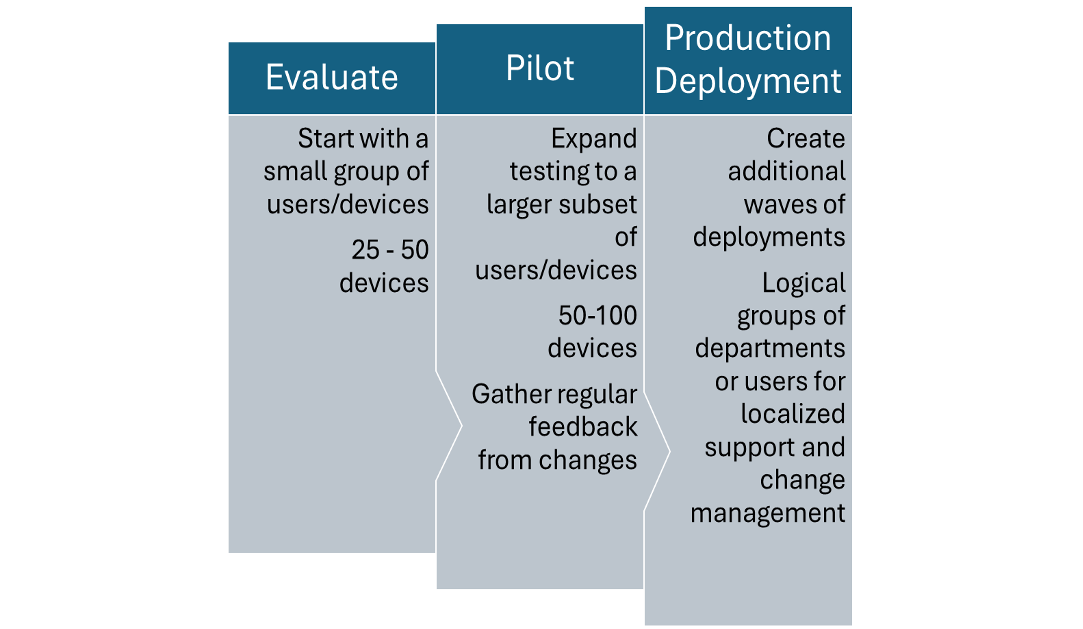
The diagram below suggests starting with a small group, such as your IT team or a partner team, to evaluate changes. Then, pilot the changes with a larger group before gradually expanding the scope to cover the entire organization.
Securing identities involves using MFA and segmenting access with Microsoft Entra Conditional Access. These features require an incremental adoption process, as users may need to be informed about transitioning from passwords to MFA methods.
When planning, consider:
- The need for user buy-in for mobile app-based MFA versus token-based approaches like FIDO2 or Windows Hello for Business.
- Piloting and gradually rolling out Conditional Access policies due to their complexity.
- Evaluating endpoint health, patch status, and location in Conditional Access parameters, requiring endpoint management enrollment.
- Integrating modern apps with MFA and Conditional Access, knowing the number of applications and their authentication methods is crucial.
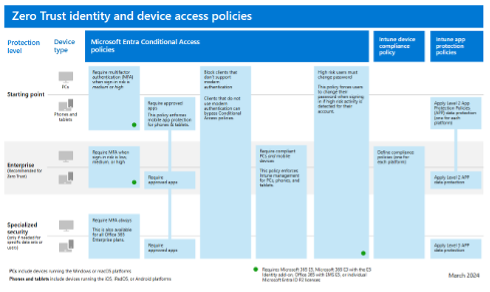
Use resources from Microsoft, such as the Common Zero Trust identity and device access policies set, to secure remote and hybrid work environments effectively.
Here are the policies for three levels of protection.
This policy set includes a Starting point protection level with minimal user impact and doesn’t require device management enrollment. Once devices are enrolled, you can deploy the recommended Enterprise level for Zero Trust.
To incrementally increase the scope of policies:
- Start with a small group of users and gradually include more, mitigating risk by targeting specific users or devices.
- Begin with Microsoft 365 apps and services, then expand to other SaaS apps and eventually apps built in Azure or other clouds.
Remember, user adoption and communication are critical. Security initiatives often fail due to disruption and poor communication. Executive support is crucial as early adoption by leadership encourages wider acceptance.
Microsoft provides end-user rollout templates and materials for education and adoption at https://aka.ms/entratemplates.
Build and test
After assembling your team, reviewing resources, and developing a project deployment plan, ensure it is well-documented. Before adopting the plan, test configurations in a test environment.
Each technical area, such as Conditional Access policies, can secure functionality across the tenant, but misconfigurations can lead to issues like locking out administrators. To reduce risk, use a test or QA tenant that mirrors your current environment to implement and familiarize yourself with features.
Refer to the RAMP Checklist to track progress through planning and implementation steps. The QA tenant will serve as the test bed before transitioning to the production tenant, where changes are applied incrementally.
As you deploy new configurations, maintain clear communication with users and monitor impacts. Security features may have a low technology impact yet a high process impact, and vice versa. Testing each service’s impact is crucial, as some effects might only become evident during production piloting.
Keep track of governance and management changes
The very goal of Zero Trust is to incrementally increase security and implement changes in the environment that achieve this goal. These changes require changes in the management and governance models of the environment. As testing and deployment occurs, be sure to document the changes and impacts to the management and governance model.
Phase 4: Adopt Zero Trust for Remote and Hybrid Work
During this phase, strategies and deployment plans are gradually implemented across functional areas. This phase involves a broader execution of the proof of concept. The deployment plan is carried out, with rollout occurring in successive waves based on user segmentation and targeted areas within the digital estate.
Each new configuration should be deployed into the production tenant as a limited proof of concept.
Even after testing new configurations in QA, document your production deployment plans, including tests, evaluations, and success criteria. Start with low-impact users, endpoints, and apps before expanding. Learn from each implementation phase to update the plans. Be aware that some functionality, even if deployed to a limited audience, can affect the entire service. Mitigate this by identifying risks during QA testing and having a roll-back plan.
A successful deployment plan includes the following elements:
- Adoption and rollout plan to include the user communication strategy
- Executive adoption and rollout plan to ensure executive endorsement
- User adoption and rollout plan
- Project management and governance artifacts
- User segmentation by business unit or user impact
- Device segmentation by business unit or user impact
- Apps ranked by criticality and complexity of implementation
- Draft updates for changes in day-to-day management and governance
Stage 5: Governing and Managing Zero Trust
Security governance is iterative. For organizations with existing security policies, adopting Zero Trust can evolve those policies. As security strategy evolves, so do cloud governance processes.
In planning, new functionality was tested in a test tenant. Implementing Zero Trust features requires a different management approach for the resulting end-state.
Here are some examples of new requirements for this scenario:
- Establish a process to approve administration access when required as opposed to standing admin access.
- Update lifecycle management of users as they enter, use, and exit the organization.
- Update the lifecycle management of devices.
- Update the release criteria for new apps to ensure they are included in the scope of conditional access policies.
As the rollout progresses, management must adapt its methodology to changes in governance. Zero Trust influences how the environment is monitored and requires mandatory identity object lifecycle management. Object attestation ensures accountability shifts from IT to the business. Zero Trust increases estate administration maturity, affecting user and administrator interactions. See the table below for potential changes.

Additional resources for day-to-day governance and operation include:
Using a Trusted Security Partner to Implement Your Zero Trust Framework
The Zero Trust Model combines policies, processes, and technology to establish trust from cloud to edge, irrespective of where users access the network. Unlike traditional protection methods that rely on network firewalls and VPNs, Zero Trust does not presume any user identity or device is secure on any network. Instead, it mandates continuous verification of user identity and device, along with monitoring network, data, and application security.
As you work to deploy the Zero Trust Framework into your environment, using trusted partners like Quisitive’s Spyglass Coaches can help you implement the technical controls while also providing ongoing advisory services for business enablement and ensuring that workflows do not hinder the business.

;)