Managed IT Security Services
Our expert cloud security services seamlessly extend your IT team with 24/7 protection and continuous optimization across Microsoft Azure, Dynamics, and M365.
Avoid costly rip-and-replace solutions. Our Spyglass® program integrates with your existing teams, tools & processes.

Your Microsoft Security Partner of Choice
Unlike traditional MSSPs, we focus on prevention, not just response—identifying root causes and closing security gaps before threats escalate. No rip-and-replace. No extra tools—just smarter use of the Microsoft technology you already own.
Control who can access systems and data, helping prevent breaches and enforce secure, role-based access.
- Multi-Factor Authentication
- Single Sign On
- Risk-Based Access Control
- Self-Service Password
- Secure Cloud Administrators
- Entra ID (Azure Active Directory)
Automate user account setup and removal, reducing manual work and closing security gaps from inactive accounts.
- Onboarding
- Provisioning
- Permissions Management
- Offboarding
- Automated Reporting
- Historical Reporting
Centralize control of IT systems to improve performance, reduce downtime, and simplify maintenance.
- Mobile Device Management
- Workstation Management
- Update Deployment
- Endpoint Protection
- Unapproved Device Controls
- Disk Encryption
Secure sensitive data with encryption and access controls to prevent leaks and support compliance.
- Automatic File Classification & Encryption
- Application & Data Containerization
- Cloud-based Data Loss Prevention
- Encrypted Email
- Secure External Data Sharing
Get real-time visibility into system health so teams can quickly catch and fix issues before they escalate.
- Automatic File Classification & Encryption
- Compromised Account Detection
- Compliance and Policy-Driven Alerts
- Shadow IT Detection
- Utilization Metrics to Drive Success
Identify and fix security weaknesses to reduce risk and keep systems protected against threats.
- Exposure Management
- External & Internal Vulnerability Scans
- Patch Management
- Automated State Monitoring
- Monitoring and Remediations
Control who can access systems and data, helping prevent breaches and enforce secure, role-based access.
- Multi-Factor Authentication
- Single Sign On
- Risk-Based Access Control
- Self-Service Password
- Secure Cloud Administrators
- Entra ID (Azure Active Directory)
Automate user account setup and removal, reducing manual work and closing security gaps from inactive accounts.
- Onboarding
- Provisioning
- Permissions Management
- Offboarding
- Automated Reporting
- Historical Reporting
Centralize control of IT systems to improve performance, reduce downtime, and simplify maintenance.
- Mobile Device Management
- Workstation Management
- Update Deployment
- Endpoint Protection
- Unapproved Device Controls
- Disk Encryption
Secure sensitive data with encryption and access controls to prevent leaks and support compliance.
- Automatic File Classification & Encryption
- Application & Data Containerization
- Cloud-based Data Loss Prevention
- Encrypted Email
- Secure External Data Sharing
Get real-time visibility into system health so teams can quickly catch and fix issues before they escalate.
- Automatic File Classification & Encryption
- Compromised Account Detection
- Compliance and Policy-Driven Alerts
- Shadow IT Detection
- Utilization Metrics to Drive Success
Identify and fix security weaknesses to reduce risk and keep systems protected against threats.
- Exposure Management
- External & Internal Vulnerability Scans
- Patch Management
- Automated State Monitoring
- Monitoring and Remediations
We provide continuous support to ensure that your security posture management stays strong.
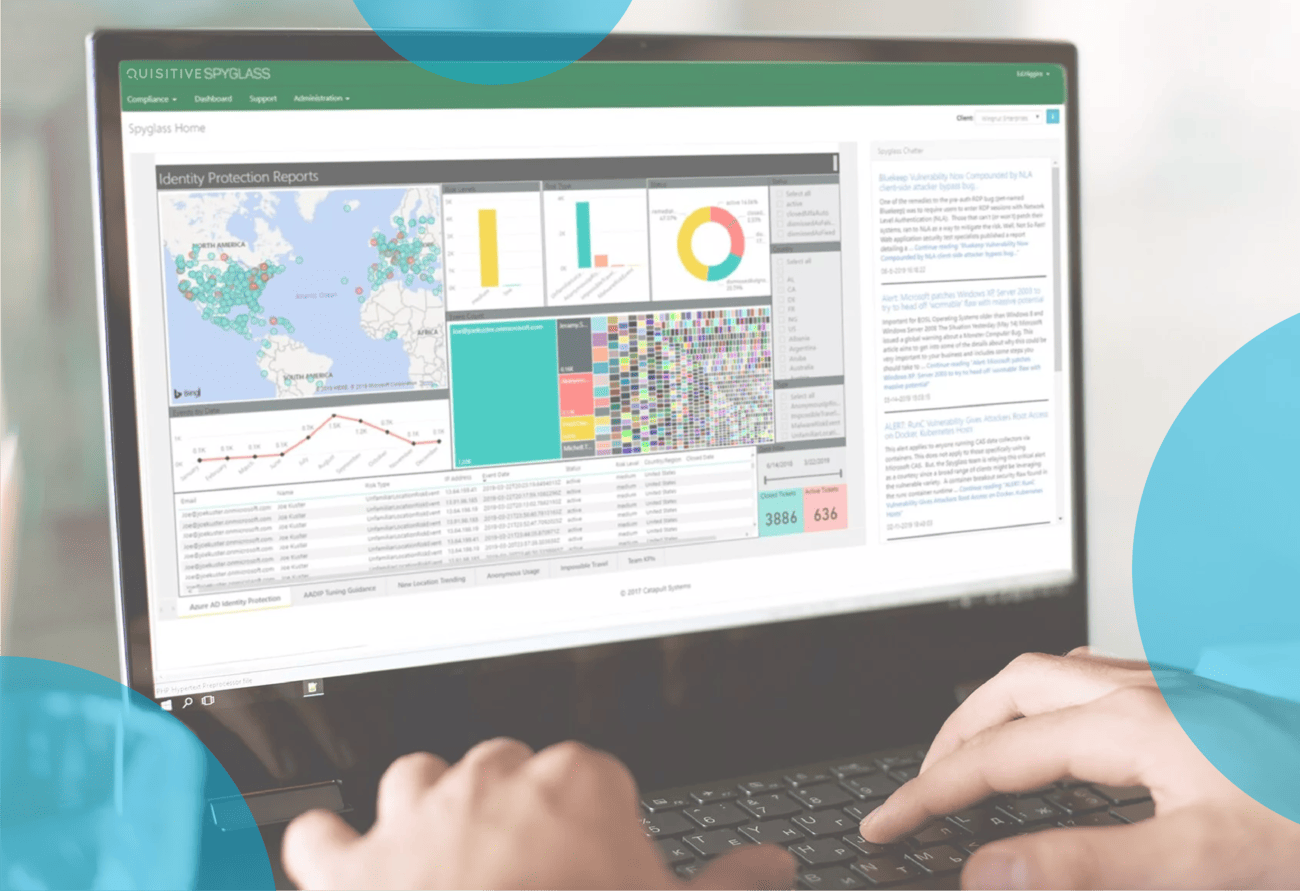
With Spyglass®’s easy-to-use dashboard, administrators can quickly track and manage compliance goals to ensure the appropriate policies and controls are in place.

Spyglass combines expert security advising with a custom cloud solution built on your Microsoft technologies.
We tailor a framework to your needs, align policies, and provide ongoing guidance to manage and strengthen your security posture.

Gain a clear view of your security posture with expert guidance and ongoing analysis from a dedicated security advisor.
Quisitive’s Managed IT Security Services give you access to specialists for a predictable monthly cost.


As a member of the Microsoft Intelligent Security Association, Quisitive is recognized as a managed security service provider (MSSP) that integrates our solutions with Microsoft Security technology to better defend customers against a world of increasing cyber threats.

Microsoft Solutions Partner
As a top Microsoft Solutions Partner with a designation in Security, we hold specializations in...



