As we move forward into 2025, significant updates to the HIPAA security rule are on the horizon. These changes are designed to enhance the security protocols for healthcare providers, health plans, and their business associates. The focus is on preventing phishing and ransomware attacks, ensuring end-to-end encryption, and implementing multi-factor authentication (MFA). Here’s a detailed look at what these HIPAA updates entail and how leveraging the Microsoft stack can help meet these new requirements.
During a recent webinar, I cited the significantly sharp increases in cybersecurity breaches in the last several years and the continuation of those trends where bad actors are “upping their game” to launch ransomware attacks and data theft.
Please see the illustrations below, as citations from US Health and Human Services (Breach Report), a database of all data breaches greater than 500 records, that provides clear and irrefutable proof of these increases:
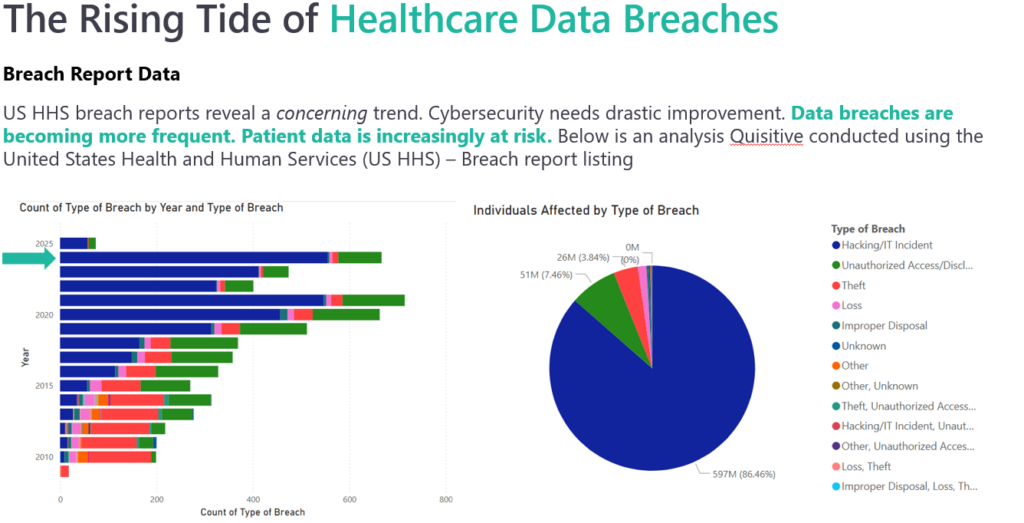
Key 2025 HIPAA Updates
1. Expanded Responsibility:
The new rules extend the responsibility for security protocols to business associates, not just covered entities. This means any company providing services to or on behalf of a covered entity must comply with the new regulations.
2. Stronger Cybersecurity Controls:
The updates emphasize stronger security controls, spanning from asset inventory and configuration management to ePHI encryption for data at rest and in motion to mandatory MFA to vulnerability and patch management. Below is the list of technological requirements that must be met:
- Multifactor-Authentication Deployed and Enforced
- Encryption of ePHI at rest, Network map of ePHI dataflows
- Vulnerability and Risk Analysis for Assets related to ePHI
- Endpoint and Server protection (anti-malware, removing extraneous software, disabling network ports)
- Stronger security incident response plans, including backup & restore within 72 hours
- Network Segmentation
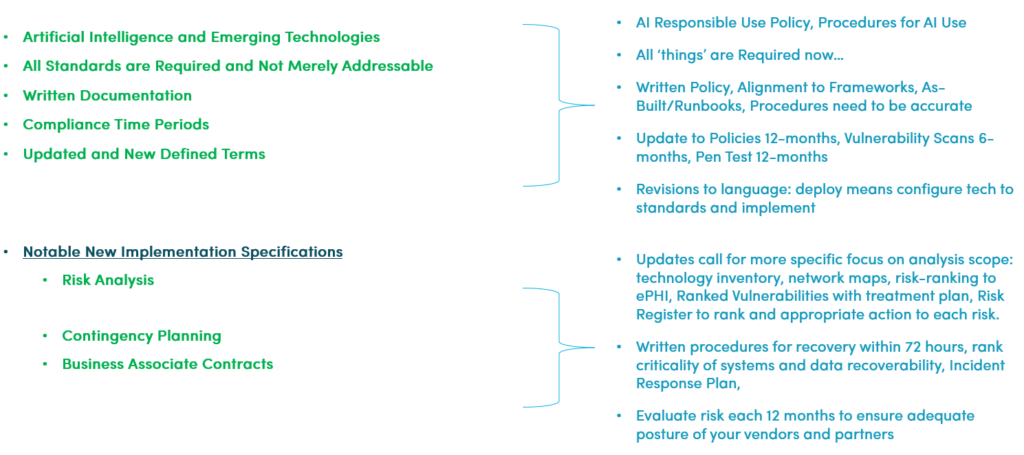
The new law brings with it also administrative controls (non-technical requirements) that must be met:
- Artificial Intelligence and Emerging Technologies
- All Standards are Required and Not Merely Addressable
- Written Documentation
- Compliance Time Periods
- Updated and New Defined Terms
- Risk Analysis
- Contingency Planning
- Business Associate Contracts
For the administrative controls, I provided some examples and excerpts from the law to help demystify what is required as illustrated below:
3. Incident Response and Breach Reporting:
With these HIPAA updates, there are now tighter timeframes for reporting breaches, requiring continuous monitoring protocols and disaster recovery plans to be in place.
Leveraging the Microsoft Stack
For the technological requirements I mentioned, Quisitive works as a partner to Microsoft to implement controls using several tools and features that are included within the Microsoft M365 and Azure Security Stack as illustrated below

To further provide examples, please see the following:
- Identity and Access Management:
- Microsoft Entra ID: Enforce MFA using the Authenticator app or passkeys to secure user identities.
- Conditional Access: Implement risk-based conditional access policies to ensure only authorized users can access sensitive data.
- Data Encryption and Protection:
- Microsoft Purview: Use Purview for data classification, labeling, and encryption to protect sensitive health information.
- Microsoft Priva: Manage privacy and compliance requirements, ensuring data protection and regulatory adherence.
- Vulnerability and Risk Management:
- Microsoft Defender: Utilize Defender for endpoint protection, vulnerability management, and risk analysis.
- Microsoft Intune: Integrate with Defender to automate patch management and configuration changes.
- Incident Detection and Response:
- Microsoft Sentinel: Deploy Sentinel for advanced threat detection, incident response, and security orchestration.
- Security Copilot: Leverage AI-driven insights to enhance security operations and automate remediation processes.
The New Law (pending) is all about Industry Best Practices
Despite political processes and deliberation about the new updates to HIPAA law, the changes proposed in the HIPAA 2025 law are grounded in industry best practices. These practices are essential for ensuring the security and privacy of sensitive health information. Implementing these measures not only helps in compliance but also significantly enhances the overall security posture of healthcare organizations.
Conclusion
The forthcoming 2025 HIPAA changes underscore the need for robust security measures in the healthcare sector. By leveraging the comprehensive tools and solutions offered by the Microsoft stack, organizations can ensure compliance with the new regulations and protect sensitive health information effectively.
I hope this helps you understand and anticipate what will need to happen in order to comply with this new law when it becomes enforceable. Quisitive stands ready to help you.
Till next time,
Ed Higgins
(CISSP, CISA, CISM, CGEIT, C/CISO, TXPI)
Executive, Director Security and Compliance Solutions, Security Office Leader
HIPAA Compliance Made Easy with Quisitive
As a Microsoft Intelligent Security Association (MISA) member and Managed Security Service Provider (MSSP), Quisitive is uniquely positioned to help organizations navigate the complexities of cybersecurity.
Quisitive’s Spyglass HIPAA 2025 Quick Start Program is designed to help you swiftly and confidently meet compliance mandates through proven cybersecurity best practices. With our HIPAA 2025 Quick Start, your organization will get:
- Comprehensive Security & Compliance Strategy
- Security Operations & Threat Detection
- Data Security & Ongoing Protection
- Incident Response & Recovery
- Security Program Optimization

;)



