Security is a never-ending pursuit. Bad people exist and we must continually find ways to combat their evilness. Let’s examine a very small portion of how Microsoft Azure is thwarting this criminal activity.
The CPU Cache Vulnerability
On 1/3/2018 the world was informed that almost every computer on earth was susceptible to the “CPU data cache timing” exploitation. How did Azure handle the vulnerability?
- Azure PaaS customers were fixed before the public announcement
- Azure IaaS VM customers utilizing Availability Sets were fixed under the normal patch process
- Other IaaS VM customers were notified and a coordinated fix delivered with minimal business disruption
While many data centers struggled with implementation, Azure customers felt little pain.
Azure Security Facts
- Global Telemetry is used to analyze, recognize, and react to threats
- Threat Intelligence monitoring is continually looking for bad actors
- Statistical Profiling is used to build a historical deployment baseline
- Machine Learning (ML) leverages this baseline to detect anomalies in your subscriptions
- ML is used to recommend VM application white listing rules
- Behavioral Analytics is used to discover malicious attacks by applying known patterns to your baseline subscription data
In short, Azure is using AI as one of many components to ensure your resources are secure and so far… its working.
Muscle
Microsoft counts on 3500+ Security Engineers to stave off over 1.5 million Azure hack attempts per day. Departments helping to combat these attacks include Microsoft Digital Crimes Unit (DCU) and Microsoft Security Response Center (MSRC). Now couple these with Microsoft’s Cyber Threat Intelligence program and you have an unmatched global security posture.
Microsoft is also a member of the Cloud Security Alliance, which is dedicated to establishing and promoting security first best practices for cloud computing and provides education and certification around these practices. Corporations and communities are realizing it takes a unified army to combat the forces of hacker evil.
Assumed Breach Strategy
Azure uses it and you should as well. This new (now old) strategy has helped reshape threat response thinking. Instead of taking the typical reactionary approach, make the effort to institute your own proactive Incident Response Plan and practice it. This exercise will put your organization in a far better position to deal with the breach when it happens.
Below are some of the top reasons intrusions happen within an organization.
- Old unsupported software, databases, and drivers
- Careless Employees
- Mobile devices (BYOD)
- Third-Party services
- Custom development
- Phishing attacks
- Unlicensed software
- Dated infrastructure
There are myriads of other violations that wreak havoc within organizations daily. Use the ‘Assume Breach Strategy’ to ensure your organization is postured for quick intrusion remediation.
Azure Security Center (ASC)
We’ve established a bit about security around Azure, what Microsoft is doing to combat these evil hacker, and what we should do to prepare. Now let’s dive into ASC and see how it can help your Azure subscriptions maintain ‘business as usual’.
- What is ASC?
- Policy Management
- Perpetual Security Assessments
- Actionable Recommendations
- Advanced Cloud Defenses
- Prioritized Alerts and Incidents
- Integrated Security Solution
- What are some of the ways ASC implements these components?
- Through health monitoring, which uses a proactive resource auditing strategy to identify systems that are not within organizational compliance
- Through analysis, which formulate recommendations and automates fix implementation
- Through managed access utilizing Just-in-time VM access, which reduces systems exposure
- Through adaptive application controls, which analyzes, using ML, VM processes and suggests app whitelisting rules
- Through alert management and response, which integrates all your resources and then compiles, analyzes, prioritizes, and presents them for action
- Through partner integrations, so you can bring your favorites to the playground such as firewall and end point protection toys
ASC comes in two favors FREE and Standard tier. Find pricing details here. There is minimal setup to get started and the Quickstart Guide will get you up and running in a hurry.
ASC Portal Interface
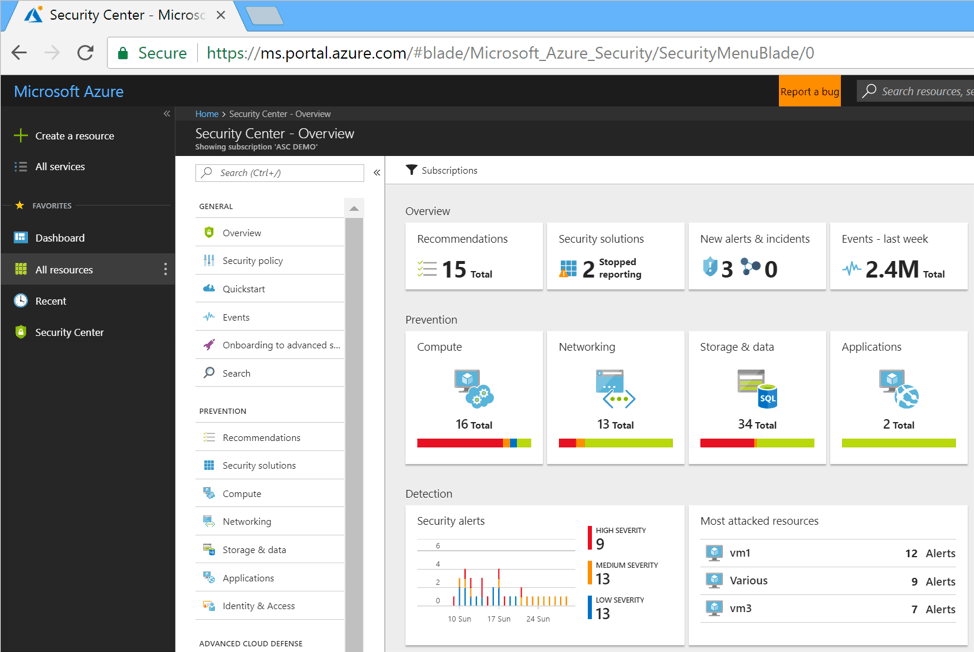

;)


