As AI companions like Microsoft Copilot become embedded in daily workflows, organizations must rethink their security posture. Traditional perimeter-based models are no longer sufficient. The Zero Trust model—built on the principles of “never trust, always verify”—offers a robust framework to secure AI integration across Microsoft 365, Security Copilot, and custom Copilot Studio deployments.
Why Zero Trust for AI?
AI companions operate across vast data surfaces—emails, documents, chats, and third-party integrations. This expanded access increases the risk of data leakage, compliance violations, and insider threats. Zero Trust mitigates these risks by enforcing:
- Explicit verification of users, devices, and applications.
- Least privilege access to minimize exposure.
- Assumption of breach to drive continuous monitoring and adaptive controls.
Layered Protections for Different Copilot Types
Microsoft outlines a tiered approach to securing AI companions and as you enable these agents, you should be enabling these layered controls along the way in line with the Zero Trust Principles.
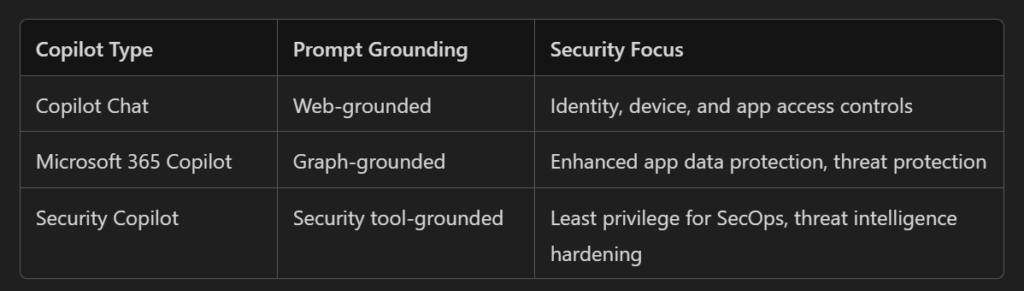
- Copilot Chat generates web-grounded prompts; these are also accessible within Microsoft 365 Copilot when the work/web toggle is switched to ‘web’.
- Microsoft 365 Copilot provides graph-grounded prompts when the work/web toggle is set to ‘work’.
- Microsoft Security Copilot delivers prompts that are grounded in your security tools.
To look at this in another view, let’s look at the below:
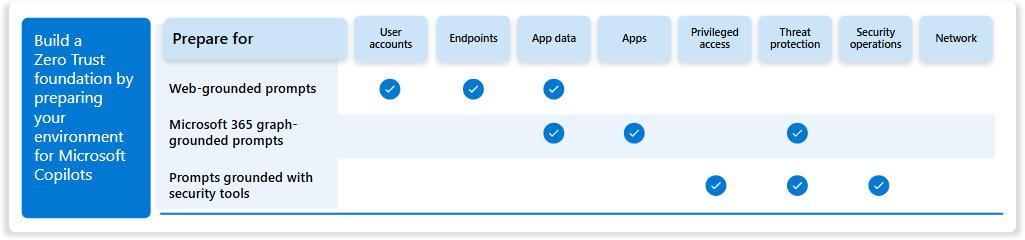
To effectively implement Zero Trust for Microsoft 365 Copilot, it is essential to secure your tenant across the following seven layers:
Data protection
- Implement encryption, data loss prevention, and regular audits to safeguard sensitive information from leaks or unauthorized access.
Identity and access management
- Utilize strong authentication methods, enforce least privilege access, and continually monitor user identities and permissions to prevent unauthorized entry.
Application protection
- Deploy security measures such as app governance policies, vulnerability management, and application whitelisting to reduce risk from compromised or malicious apps.
Device security
- Ensure that all devices are compliant with organizational policies through endpoint protection, device health checks, and regular updates to minimize vulnerabilities.
Threat defense
- Integrate advanced threat detection, incident response systems, and threat intelligence to identify and respond to potential attacks quickly.
Secure Teams collaboration
- Apply controls for secure file sharing, meeting policies, and communication encryption within Teams to protect conversations and shared resources.
User data permissions
- Regularly review and adjust user permissions to make sure individuals only have access to the data they need, reducing the risk of internal threats or accidental exposure.
Overview of how Microsoft 365 Copilot has access to your organizational data
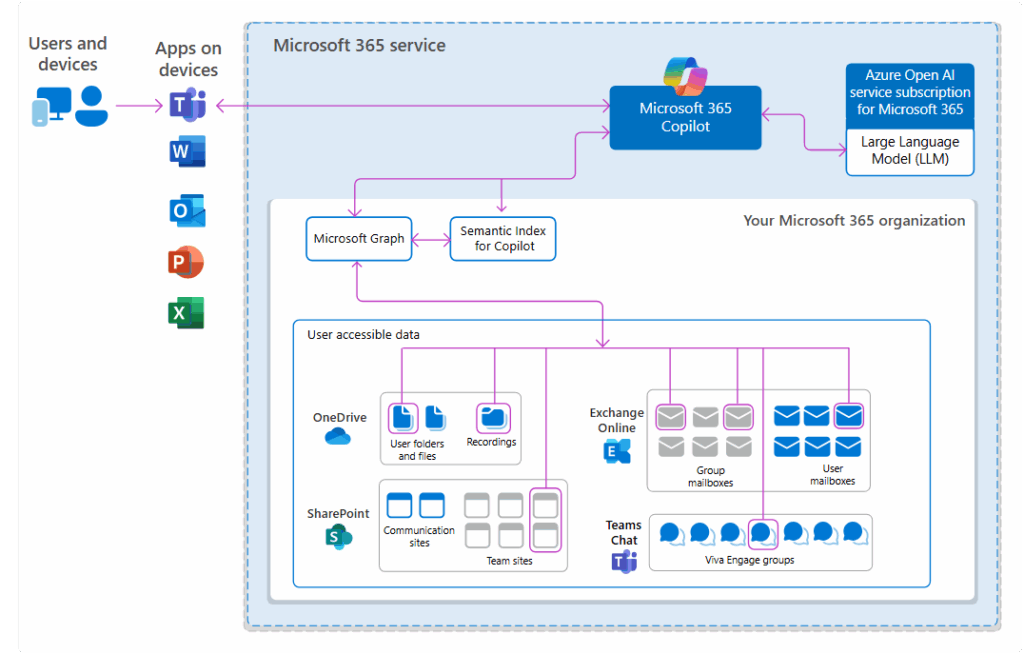
Based on the information above user devices/identities are equipped with Microsoft 365 applications, enabling users to initiate Copilot prompts.
Copilot consists of several key components:
- The Copilot service which coordinates responses to user prompts.
- The Large Language Model (LLM) utilized by Copilot to generate optimal responses.
- A Microsoft Graph instance that manages data within your Microsoft 365 tenant.
- The Microsoft 365 tenant containing organizational data.
Copilot results for each user only include data to which that user has authorized access.
Organizations may be at different stages of implementing Zero Trust protections. For each step:
- If none of the protections described have been implemented, pilot and deploy them prior to assigning Copilot licenses.
- If some of the protections are already in place, use the step as a checklist to confirm that each protection has been piloted and deployed before assigning Copilot licenses.
Refer to Copilot requirements for the most up-to-date support regarding security-related and other features of Microsoft 365.

To implement Zero Trust principles within your Microsoft Security Copilot environment, five key layers of protection should be enforced:
- Safeguard administrator and SecOps personnel accounts through comprehensive identity and access management policies.
- Enforce least privilege by assigning only essential roles to administrator and SecOps user accounts.
- Effectively manage and secure all devices used by administrator and SecOps teams.
- Deploy and verify the effectiveness of your threat protection solutions.
- Ensure secure integration and access with third-party security products connected to Security Copilot.
To start down the Strategic Implementation of Copilot or AI journey, consider the below:
- Identity and Access Management
- Enforce MFA and conditional access for all users.
- Apply role-based access control (RBAC) for Copilot admins and SecOps users.
- Use Privileged Identity Management (PIM) to manage just-in-time access.
- Device and App Protection
- Ensure Intune compliance for endpoint health.
- Use Microsoft Defender for Endpoint to monitor AI-related activity.
- Secure browser-based interactions (e.g., Edge summarization) with web content filtering
- Data Governance and Compliance
- Classify and label data using Microsoft Purview.
- Apply DLP policies to restrict sensitive data exposure via Copilot
- Monitor Copilot usage with Unified Audit Logs and eDiscovery tools
- Third-Party and Plugin Risk Management
- Vet all third-party Copilot connectors and plugins.
- Establish contractual data protection clauses with vendors
Organizational and Culture Readiness
Organizational change and cultural readiness are important elements of implementing new tools. These tools modify how users engage with workflows, data, and systems. Collaborating with the customer to document anticipated changes, user interaction with workflows, and expectations for the systems is advisable.
Train users on AI policies and proper data handling.
To ensure effective and secure use of AI systems, organizations should provide comprehensive training for all users on their AI policies. This includes clarifying acceptable use, privacy standards, and how to safeguard sensitive information. Training sessions might cover practical scenarios, such as identifying confidential data, recognizing potential risks in sharing information, and steps to mitigate breaches. Regular refresher courses can reinforce good practices and keep staff updated on evolving regulations.
Define responsibility across the AI platform, application, and organization.
Clearly defining who is responsible for different aspects of an AI initiative helps reduce ambiguity and enhances accountability. Organizations should map out roles and duties for managing the AI platform itself (such as overseeing infrastructure and compliance), individual applications (including monitoring outputs and user interactions), and overall governance (setting policies and ensuring legal alignment). By establishing clear lines of responsibility, teams can better respond to issues and maintain operational integrity.
Hold Zero Trust workshops to align stakeholders and technical teams.
Zero Trust is a security framework that requires strict verification for every user and device accessing organizational resources. Holding dedicated workshops enables stakeholders and technical teams to understand the principles behind Zero Trust, learn how it applies to AI-driven environments, and discuss strategies for implementation. These workshops foster collaboration, address concerns, and help all parties adopt consistent approaches to identity management, access control, and continuous monitoring.
Real-World Lessons from the Field
In recent engagements, teams have faced challenges such as:
- Agent sharing restrictions in non-default Power Platform environments due to Dataverse capacity overages.
- OCR limitations in SharePoint affect Copilot Studio’s ability to index image-based PDFs.
- Security gaps from legacy SMTP relay configurations and hybrid Exchange vulnerabilities.
- These underscore the need for proactive planning, layered defenses, and continuous validation.
Conclusion
Zero Trust is a continuous journey, not a one-time deployment. As AI companions evolve, so must your security strategy.
By embedding Zero Trust principles into every layer of your AI ecosystem, you not only protect your data but also empower your teams to innovate with confidence. This approach means continually assessing and verifying every user, device, and application that interacts with organizational resources, regardless of their location or previous access history. Regular workshops and training sessions should be held to align technical teams and stakeholders on the latest security practices, ensuring everyone understands the importance of strict identity management, access control, and ongoing monitoring.
With threats and technologies constantly changing, organizations must adapt their policies and defenses, leveraging tools like Microsoft Defender for Endpoint, Intune compliance, and Data Loss Prevention (DLP) to maintain robust protection. Ultimately, a sustained commitment to Zero Trust fosters a secure environment where innovation can thrive, and risks are actively managed as part of the organizational culture.

;)



